In the digital age, businesses face a relentless onslaught of cyber threats designed to steal sensitive data, cripple daily operations, and irrevocably tarnish reputations. As the attack surface expands, implementing robust cybersecurity frameworks is no longer an option, but a necessity. This comprehensive guide delves into the world of cybersecurity, exploring three powerhouse frameworks: ISO 27001, the NIST Cybersecurity Framework, and the CIS Controls. By understanding their strengths, you’ll gain the knowledge to create a 360-degree shield for your business, safeguarding it from the ever-evolving cyber threat landscape.
Key Points and Considerations:
Exponential Risks: The digital age offers immense opportunities but also exponential risks. Businesses are not just targeted for direct financial gain anymore – disruptions for political or social reasons are increasingly common.
The Human Factor: Cyberattacks often don’t just exploit technical vulnerabilities; they target the human element. Social engineering, phishing scams, and inadvertent data leaks due to employee error are major concerns.
Reputational Damage: A cyber attack’s impact goes beyond immediate financial losses. The erosion of customer trust, damaged partnerships, and potential legal repercussions can linger long after the initial breach is resolved.
Evolving Threats: Cybercriminals are constantly refining their techniques. Artificial intelligence (AI) is now being used in attacks, making them more sophisticated and harder to detect.
Regulatory Compliance: Many industries have ever-stricter regulations surrounding data security and privacy. Frameworks like ISO 27001 and NIST can be crucial in not only protecting your business but demonstrating compliance to regulators and partners.
Understanding Cybersecurity Frameworks
Cybersecurity frameworks are structured sets of guidelines and best practices designed to help organizations manage and reduce cybersecurity risks. They provide a blueprint for creating, implementing, and managing a secure IT environment. Think of them as a roadmap for navigating the complex and constantly changing world of cyber defense. The right framework can help you:
Prioritize Security Efforts: Frameworks offer a methodical way to identify your most critical assets (like customer data, financial information, or intellectual property), the vulnerabilities they face, and the level of risk you’re willing to accept. This helps you focus your resources and security measures where they’ll have the most impact.
Establish a Common Language: Frameworks use standardized terminology and concepts. This creates a shared understanding of cybersecurity goals and processes across your organization, making communication and collaboration between different departments (IT, management, etc.) much smoother.
Align with Industry Standards: Many frameworks are built upon widely-accepted industry standards. This ensures your cybersecurity posture aligns with best practices, making it easier to work with partners, satisfy regulatory requirements, and instill confidence in customers.
Demonstrate Due Diligence: Implementing a recognized framework shows a commitment to cybersecurity. In the event of a breach, this can help mitigate legal liability and minimize reputational damage with stakeholders by demonstrating you took responsible steps to safeguard data.
Continuously Improve: Cybersecurity isn’t a one-time project; it’s an ongoing process. Frameworks provide a structure for regularly assessing risks, updating controls, testing your defenses, and refining your strategies as the threat landscape evolves.
- Identify critical assets and vulnerabilities.
- Protect your systems with appropriate controls.
- Detects threats quickly and accurately.
- Respond to incidents effectively.
- Recover from attacks and restore normal operations.
(image source www.lepide.com)
Implementing ISO 27001
ISO 27001 is an international standard that outlines the requirements for an information security management system (ISMS). It’s a comprehensive approach that encompasses all aspects of information security.
Step-by-Step Guide to ISO 27001
- Commitment: Secure top management support and define your information security policy.
- Scope: Clearly define the scope of your ISMS.
- Risk Assessment: Identify risks to your information security and determine risk acceptance criteria.
- Control Selection: Choose appropriate controls from Annex A of ISO 27001 to mitigate identified risks.
- Implementation: Apply the selected controls and train your staff.
- Review and Audit: Regularly review and audit your ISMS for effectiveness.
- Certification: Optionally, seek ISO 27001 certification from an accredited body.
(image source www.infusedinnovations.com)
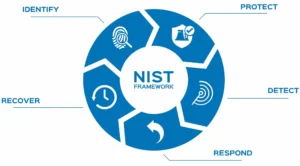
Navigating NIST Cybersecurity Framework
The NIST Cybersecurity Framework is a flexible and voluntary framework that provides a set of industry standards and best practices to manage cybersecurity risks.
Best Practices for Risk Management
- Identify: Develop an organizational understanding of managing cybersecurity risk to systems, assets, data, and capabilities.
- Protect: Implement safeguards to ensure the delivery of critical services.
- Detect: Define activities to identify the occurrence of a cybersecurity event.
- Respond: Outline actions regarding a detected cybersecurity incident.
- Recover: Plan for resilience and restore any capabilities or services impaired due to a cybersecurity incident.
(image source www.barradvisory.com)
Leveraging the CIS Controls
The CIS Controls are a prioritized set of actions that form a defense-in-depth set of best practices that mitigate the most common attacks against systems and networks.
Enhanced Cyber Defense Strategies
- Basic Controls: Focus on inventory and control of hardware and software assets, secure configurations, and continuous vulnerability management.
- Foundational Controls: Implement data protection, email and browser protections, and malware defenses.
- Organizational Controls: Conduct penetration tests, incident response management, and application software security.
Integrating Frameworks for Comprehensive Protection
While each framework can stand alone, integrating elements from ISO 27001, NIST, and CIS can provide comprehensive protection:
- ISO 27001’s structured approach to an ISMS can serve as the backbone of your cybersecurity strategy.
- NIST’s flexible framework can adapt to your specific business needs and regulatory requirements.
- CIS Controls offer a set of actionable tasks that provide immediate benefits in defending against common attacks.